Advantages:
- Automated security testing for networked control systems (NCSs), eliminating the need for manual attack scenario creation
- Reinforcement learning (RL)-based approach efficiently generates attack scenarios to identify vulnerabilities
- Proven stability using Lyapunov-based analysis, ensuring attack generation with convergence guarantees
- Adaptable across industries, including autonomous vehicles, power grids, and industrial automation
- Enhances cybersecurity strategies, allowing researchers and engineers to test and improve system defenses
Summary:
Networked control systems (NCSs) are widely used in autonomous vehicles, power grids, and industrial automation to improve efficiency and reliability. However, their dependence on networked communication and sensor data (such as RADAR sensor) makes them vulnerable to cyberattacks like false data injection (FDI) attacks, which can lead to system failures, inefficiencies, or safety risks. Currently, researchers rely on manually created attack scenarios, which lack automation and do not offer proof of convergence.
This new automated FDI attack generator solves these challenges by using reinforcement learning (RL) to develop precise, worst-case attack scenarios that test the security and safety of NCSs. The system integrates a verification cost function to evaluate system vulnerabilities, while a Lyapunov-based stability analysis ensures accurate tracking of attack impact. This first-of-its-kind tool provides an efficient, scalable, and data-driven approach to improving the security of critical networked control systems.
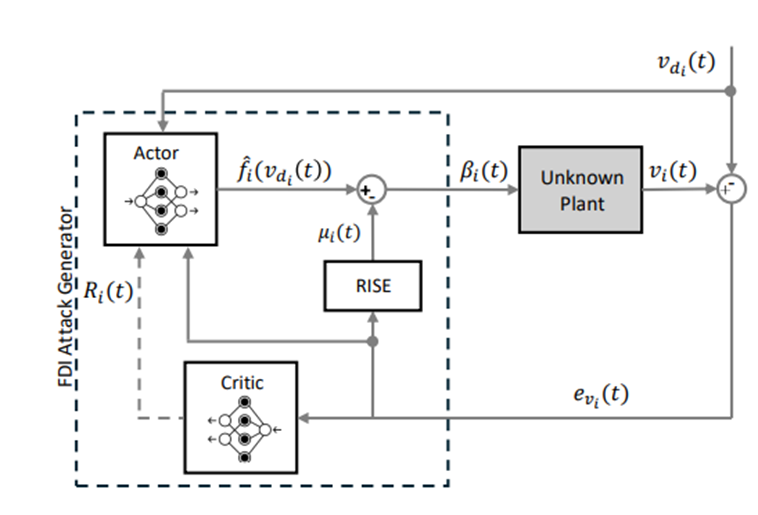
The image illustrates the Reinforcement Learning (RL)-Based False Data Injection (FDI) Attack Generator, showing how the Actor-Critic neural network model systematically injects false data into a networked control system (NCS) and optimizes attack strategies. It highlights key components like the verification cost function, RL-based attack generator (controller), and unknown plant model, ensuring precise, automated security testing for critical infrastructure.
Desired Partnerships:
- License
- Sponsored Research
- Co-Development