Competitive Advantages
- Post quantum security
- Achieves non-repudiation
- Broad applicability
- Minimal computational overhead
Summary
USF inventors have developed a mechanism to create a new cryptographic secure audit logging scheme which is also post-quantum secure. This invention ensures that an active adversary cannot generate authentication tags on behalf of the original message signer. This technique finds applications in the field of Internet of Things (IoT), medical implantable devices and payment devices.
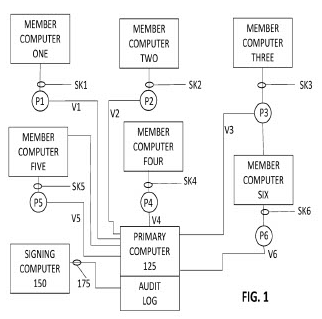
Representation of a Network of Member Computers and Verifier Parties
Desired Partnerships
- License
- Sponsored Research
- Co-Development